Accessing Internal Storage of APPLICATION using reg eDITOR Application
Windows do not allow access to the internal storage of its application even with “mass storage” mode enabled.
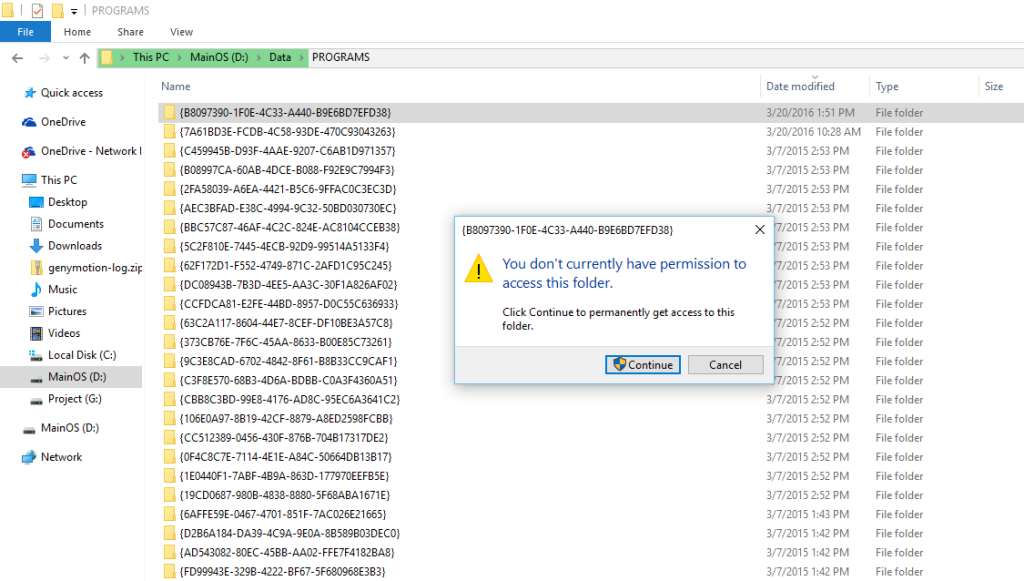
Failed To Access Internal Storage of Application Windows
To get an access to internal storage we need to perform “Interop Unlock”.
For Interop Unlock there are various procedure mentioned in “xda-developers” forum.
I have used simple techniques which allow Interop unlock on windows Lumia 920 without SD Card.
Below are the steps for the same (SD Card is not required):
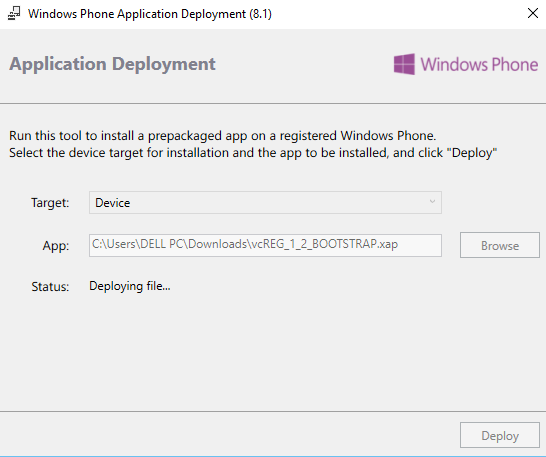
- Deploy the Application “vcREG_1_2_BOOTSTRAP.xap” using Application Deployment Tool found on location “C:\Program Files (x86) \Microsoft SDKs\Windows Phone\v8.1\Tools\AppDeploy”
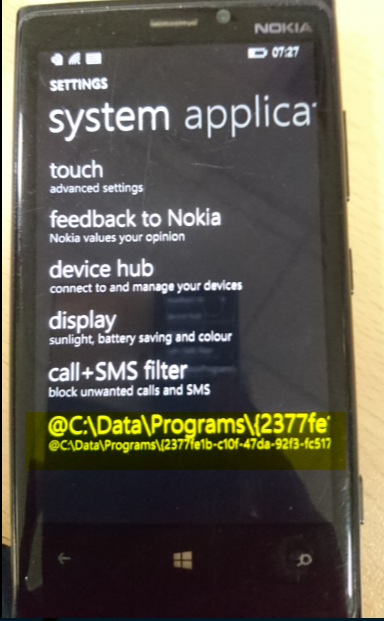
- Go to “settings” menu in the windows device, scroll download and select the highlighted application as shown in below screenshot.It will launch Lumia Registry Editor and now go to “template” menu in it
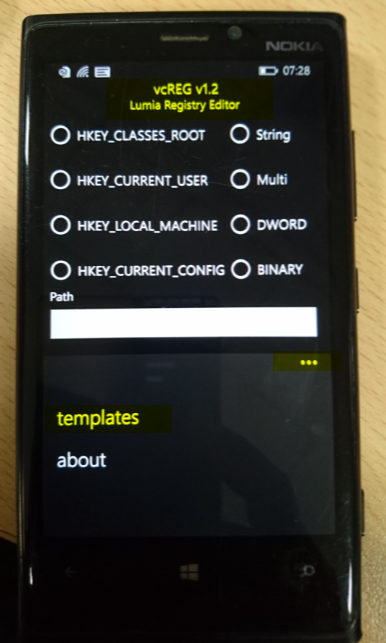
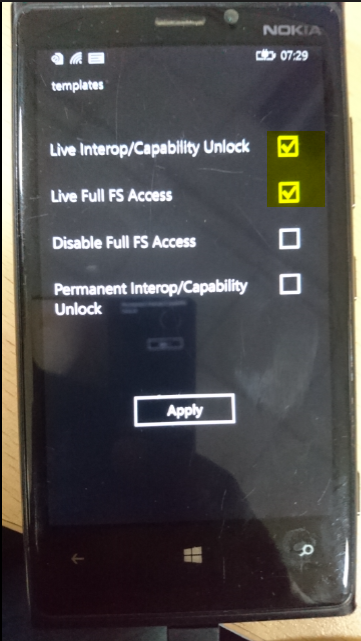
- Now reconnect the device with USB J
- Now you can access the internal storage of the applications that is being mounted on your system.
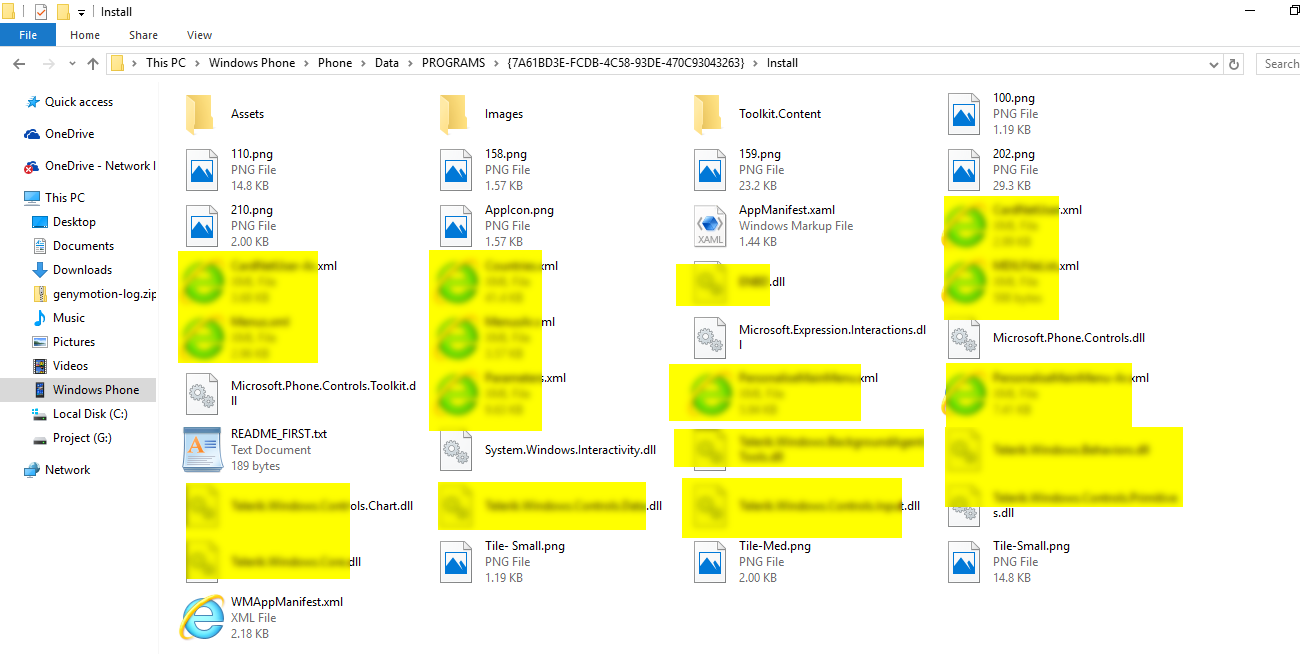
Internal Applications Storage Location: Phone\Data\PROGRAMS\{GUID}
Performing Static Analysis of XAP File
XAP is the file format used to distribute and install application software and middleware onto Microsoft’s Windows Phone 7/8/8.1/10 operating system
(Note: XAP can be installed on mobile device with the help of Application Deployment tool provided by Microsoft.)
STATIC ANALYSIS IF THE XAP FILE IS PROVIDED
- Extracting XAP file is similar to APK extraction method.
- Rename XAP extension with Zip and Extract the file
Static Analysis of the Store Application
Microsoft Store do not provide XAP file to download to check its content.
We need to perform below activities for extracting internal content of the application:
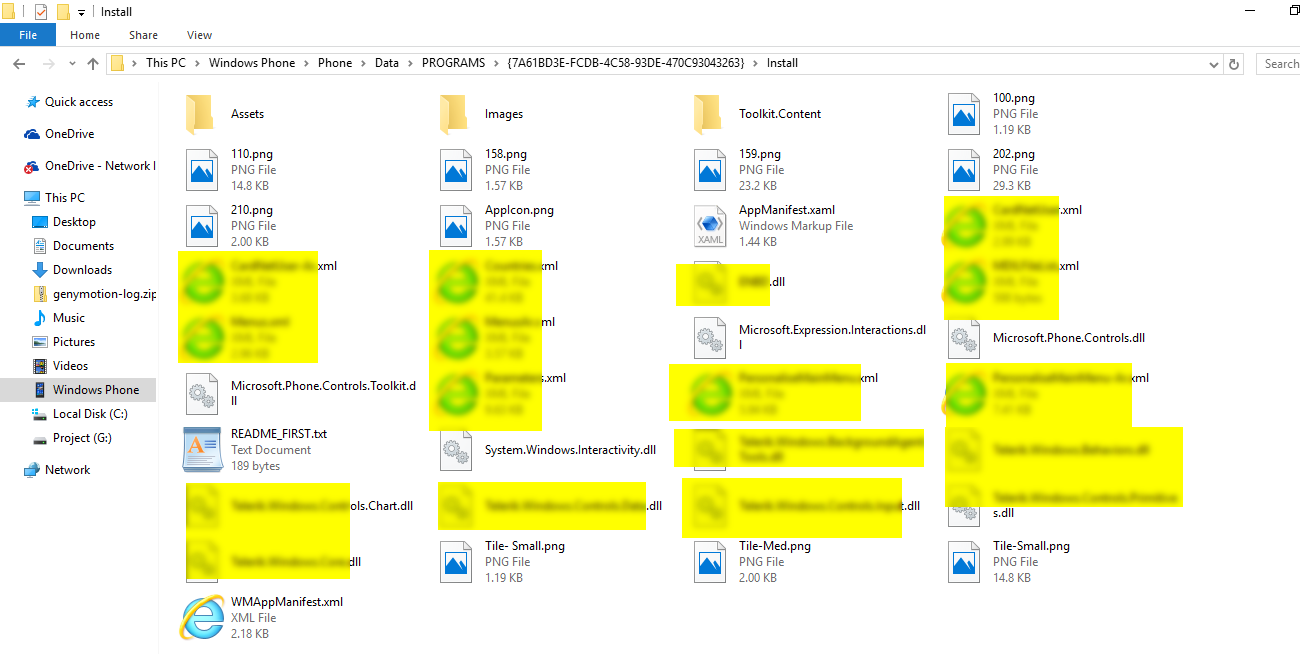
- Install the application using Microsoft Store and traverse to the location
” Phone\Data\PROGRAMS\{GUID}”
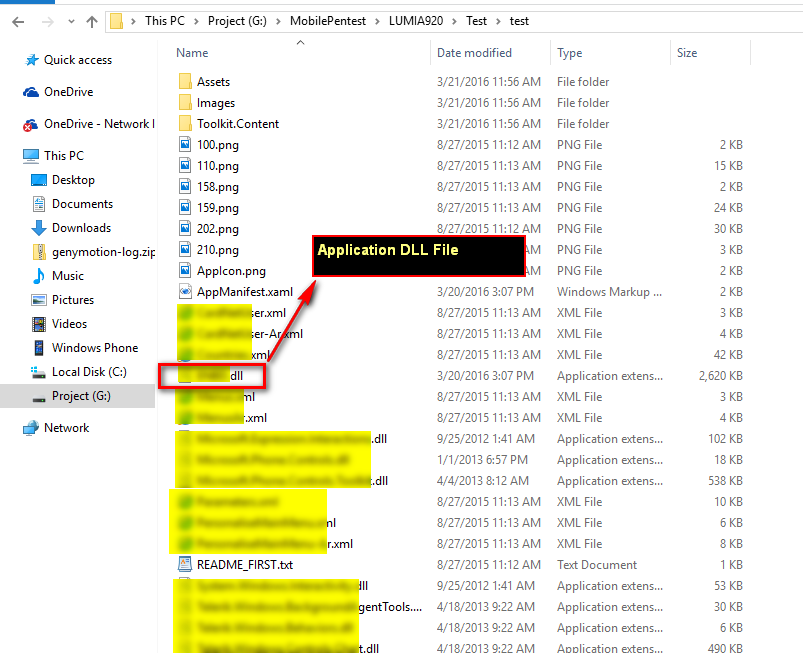
Note: GUID is application identifier. - Now we can see the application file including DLL file.
DE-COMPILE DLL File
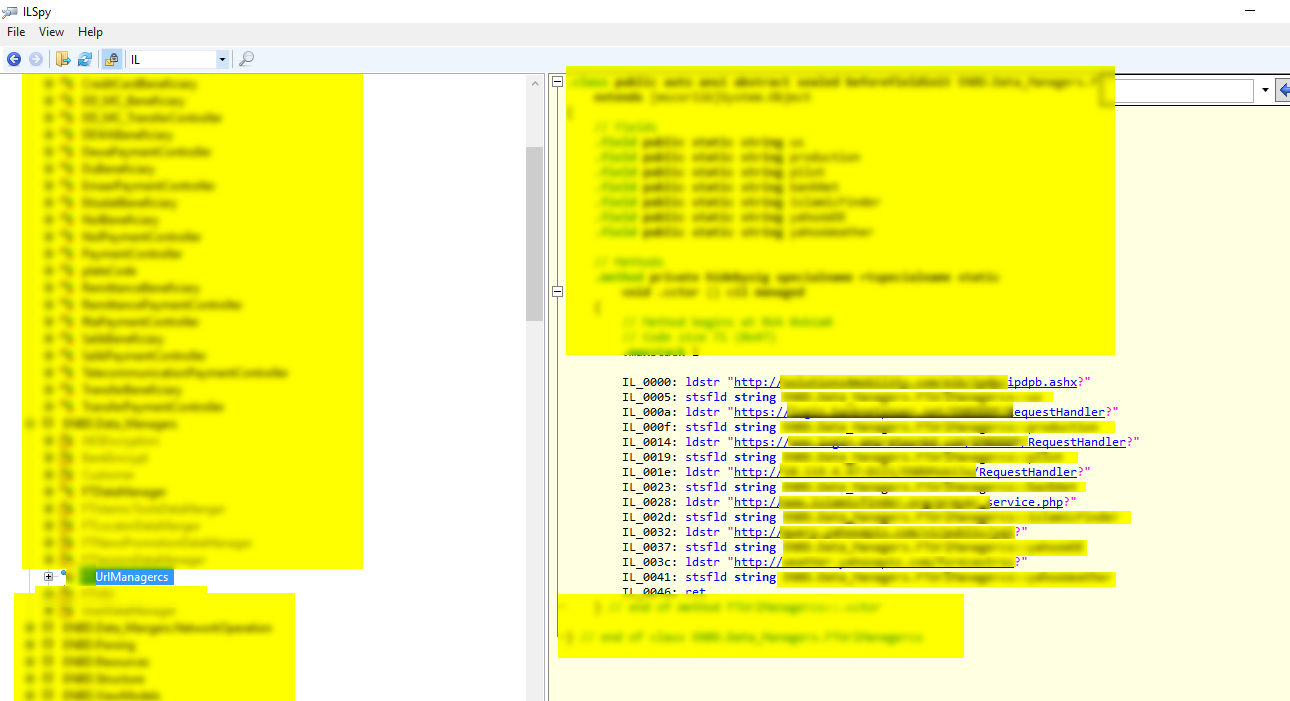
Most of XAP files contains DLL file and other resources.
DLL file can be decompiled using the various available tool.
I have used ILSpy_Master portable tool for decompiling DLL file.
WMAppManifest Verify the Application Permission
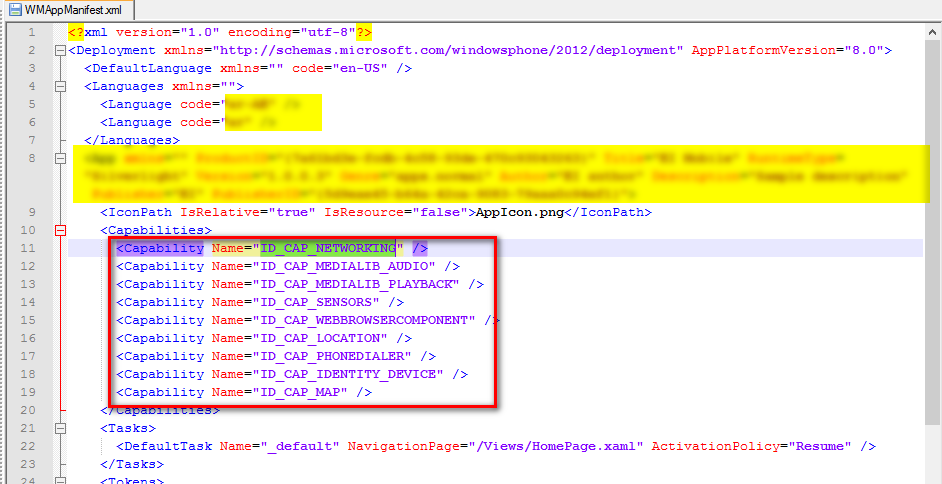
In Windows Phone, capabilities notify the end user of the security or privacy critical functionality required by the application.
Capabilities are also used to provision the security of the least privilege chamber (LPC) and reduce the attack surface by only provisioning ACLs for what the application requires.
The capabilities are configured based on application requirement. Based on the application requirement the capabilities must be reviewed.
Applications should only be assigned capabilities which they require to perform their functionality and any unused capabilities removed.
Note: You must mark the appropriate capabilities in the manifest so that the user is correctly notified of functionality that your app uses. If you don’t mark the correct capabilities, your app may exit unexpectedly when it is being installed on a user phone.
Capabilities
https://msdn.microsoft.com/en-us/library/windows/apps/jj206936(v=vs.105).aspx
Performing Dynamic Analysis of Windows Application
PERFORMING DYNAMIC ANALYSIS ON LOCAL STORAGE
Windows by default create temp location where application stores runtime information.
Windows application stores data at the runtime in the given location:
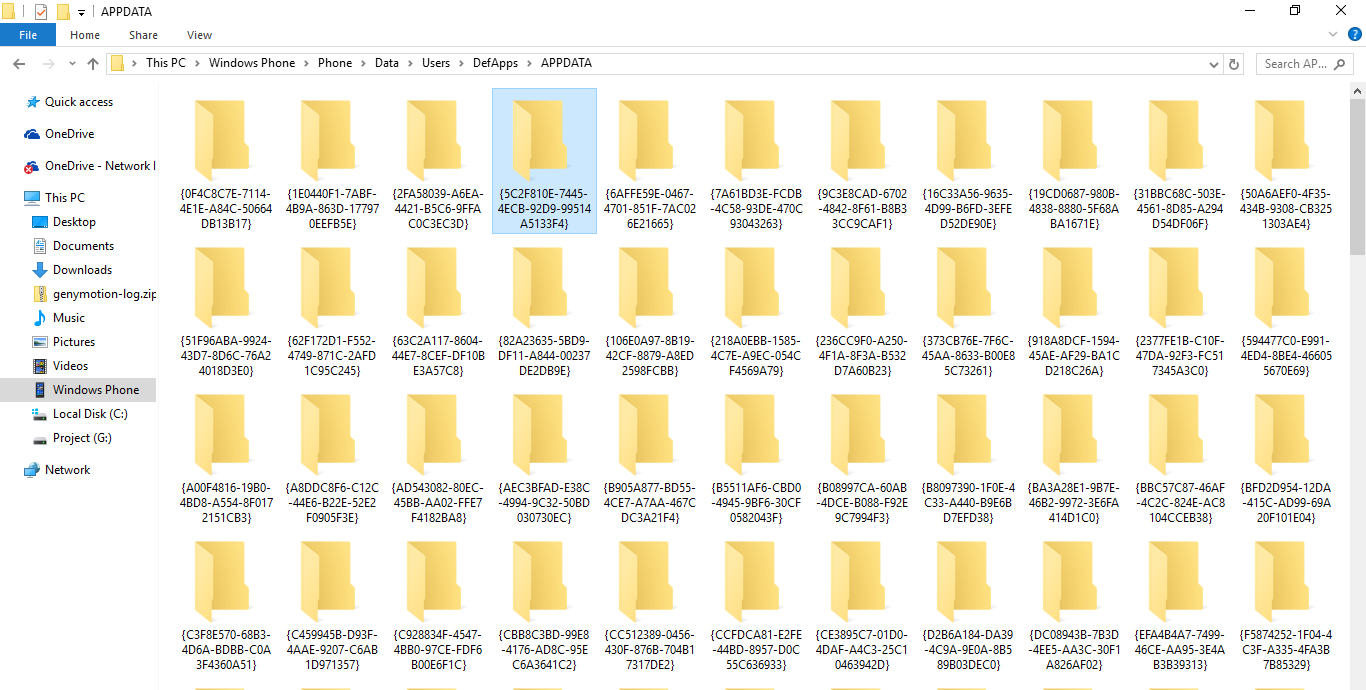
“Windows Phone\Phone\Data\Users\DefApps\APPDATA”
In the given location we may find the critical information like database(SDF) or temporary files.
INTERCEPTING TRAFFIC USING BURPSUITE
For intercepting the HTTPS traffic of Windows Phone via Burp Suite we need import burp certificates:
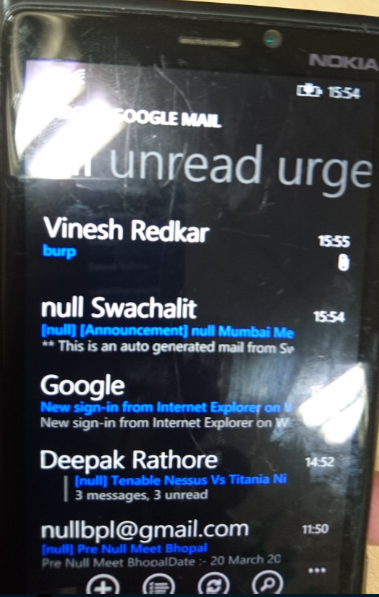
- Export Burp certificate on you operating system and then send mail to windows phone device
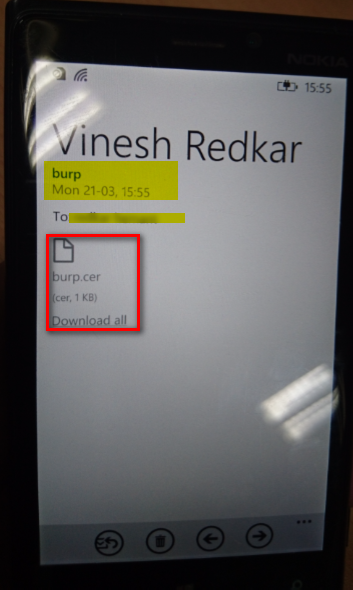
- Download the certificate on mobile device as shown in below screenshot
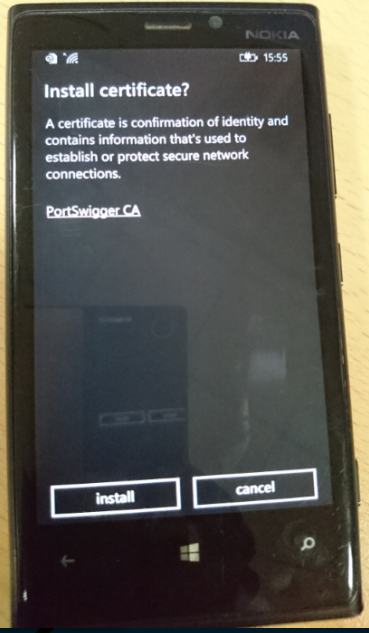
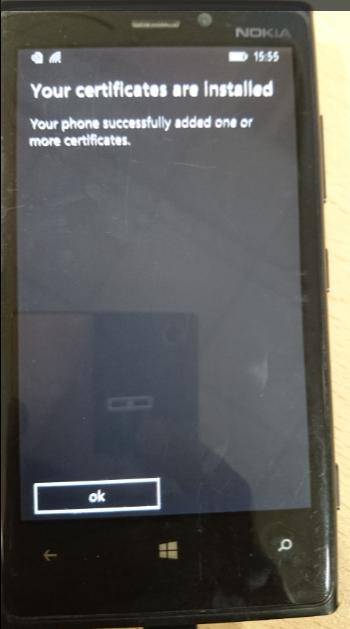
- It will ask to install the certificate kindly click install.
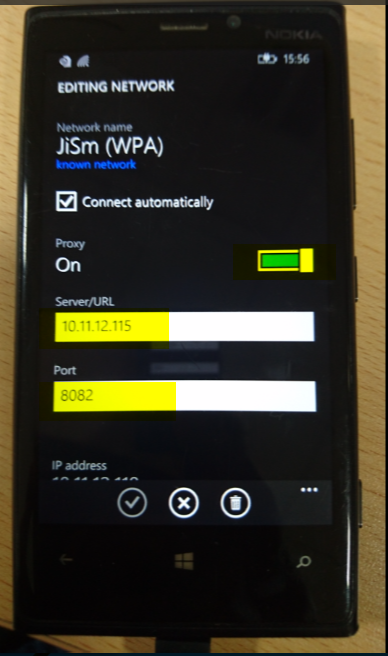
- Once done configure the burp proxy and you are good to go 🙂
- Now you can intercept HTTPS traffic from your windows mobile device.


2 Comments
Leave your reply.